Allowing third party applications in your Office 365 tenant
When managing Office 365 (and it’s related Azure Active Directory) in a large enterprise your security team is wary about allowing third party applications to access enterprise data.
Take for example the list of options that you have available in the ‘configure’ tab in Azure AD under the ‘integrated applications’ section. If you turn on the ‘Users may add integrated applications’ you will start seeing a number of applications showing up in Azure AD under the applications section. What this means is that users are accessing third party applications and using their work account as the identity.
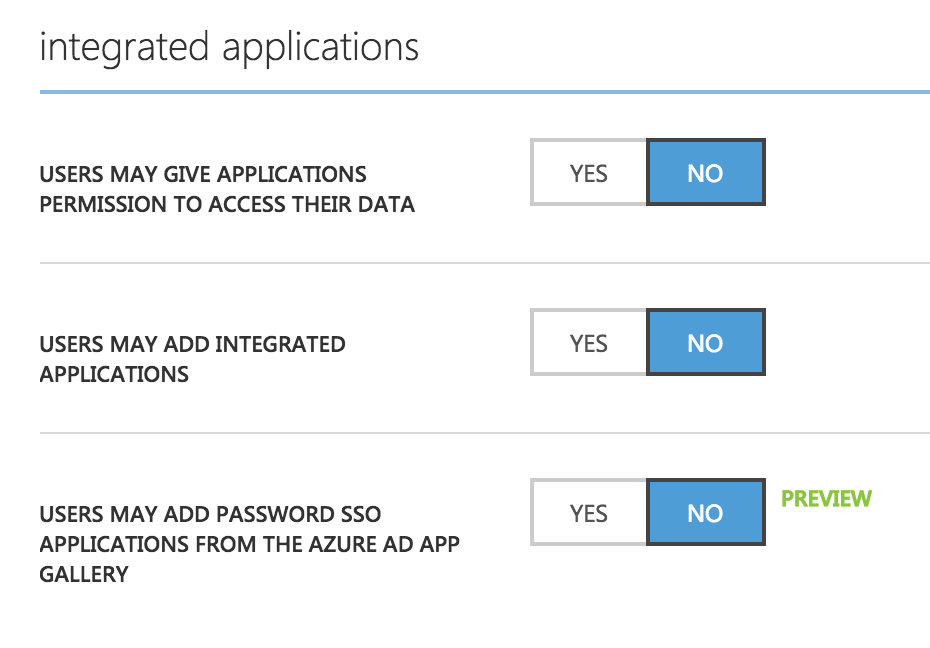
Where this gets a little scary is with the option that says ‘Users may give applications permission to access their data’. Depending on the type of permission requested by the application the user consents to in the consent page of the app (shown during the sign on process), they can potentially give third party applications access to their email, content in SharePoint Online etc. as shown by Roger from BestForTheKids.
Where I come from this is a big fat no from security. We typically require the security team vetting every SaaS application where the checks include performing vendor assessments, finding out what information is stored and how secure it is, whether the content is stored in Australia (data sovereignty).
Fine, let’s say we disable all this to prevent end users willy nilly giving third party applications access to corporate data. You will be faced with a dilemma when you have an application that has been approved (eg Microsoft’s own Fast Track portal http://fasttrack.microsoft.com) by your security team your users will still not be able to sign in to the third party app because of the above settings where we disabled users adding apps.
When a user tries to sign into the portal they will be shown an error message saying ’Sorry but we’re having trouble signing you in. We received a bad request’.
So how do you go about whitelisting only certain apps on your Office 365 / Azure Active Directory tenant? I reached out to my friends at Microsoft and this time they had an answer that made me happy.
Today the only way for an admin to consent to an application for his entire tenant is to send an interactive sign-in request with the query parameter ?prompt=admin_consent. We usually ask the app developer to invoke this request in their app somehow. But you can actually craft the request as a link yourself and have an admin click on it. There's documentation on http://aka.ms/aaddev on how to craft a sign in request. We are working on adding this capability to our portal directly so you dont have to do this.
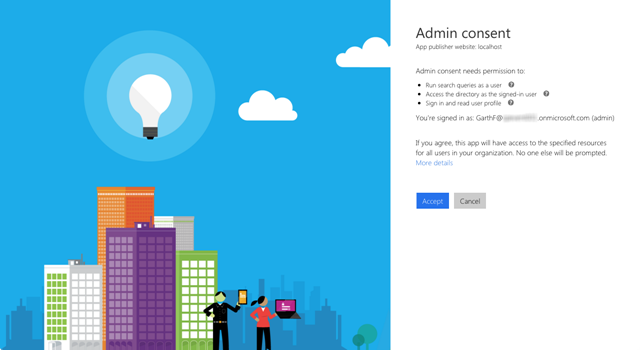
So the trick is to open a browser session in private/incognito mode and navigate to the target application (e.g. Fast Track) and try to sign in. This will redirect you to Microsoft’s login page. When you are at this page insert the ?prompt=admin_consent parameter to the query string in the the address bar and hit enter to reload the sign in page. Now sign in as a global administrator for the tenant and you will be taken to the admin consent page. Review the settings that you are approving and click on Accept. Viola you’ve now approved the app in your tenant. Now any user in your organisation can sign into the third party app without login errors and won’t even see the consent screen.