Use a custom app for Graph PowerShell delegate access
If you want to follow the least privilege model for the applications in your Azure AD tenant, you might be concerned about consenting to many permissions scopes to the Microsoft Graph PowerShell app over time.
To avoid this, you can register your own app for use with Microsoft Graph PowerShell. This allows you to have more granular control.
Here are the steps to go about setting it up.
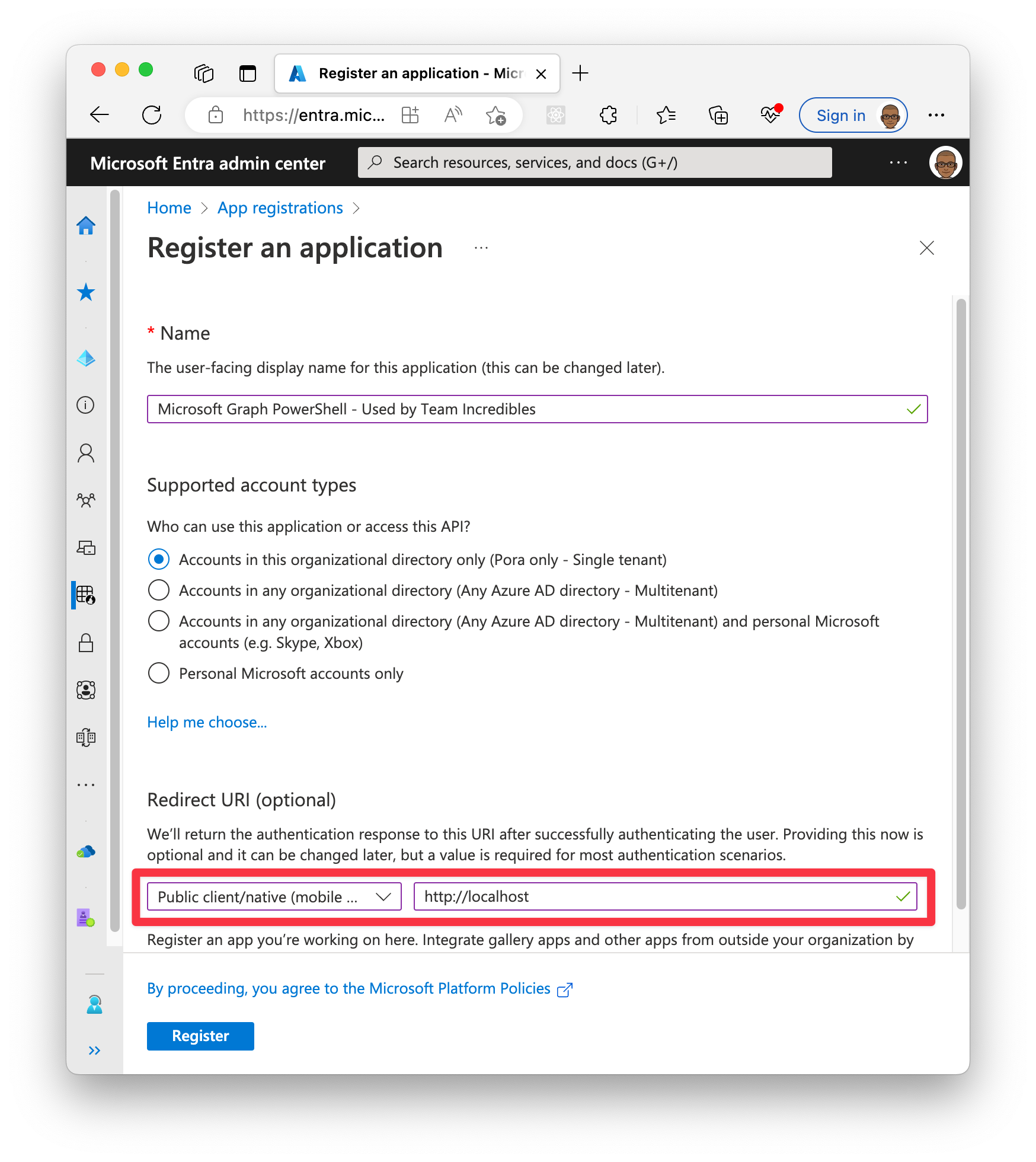
- Browse to Entra > App registrations [adappreg.cmd.ms] > New Registration
- Name: Microsoft Graph PowerShell - High Privilege admin use only (<- Give a meaningful name)
- Account type: Accounts in this organization directory
- Redirect URI:
- Select Public client/native from the drop down
- Uri: http
://localhost
- Click Create
That’s it!
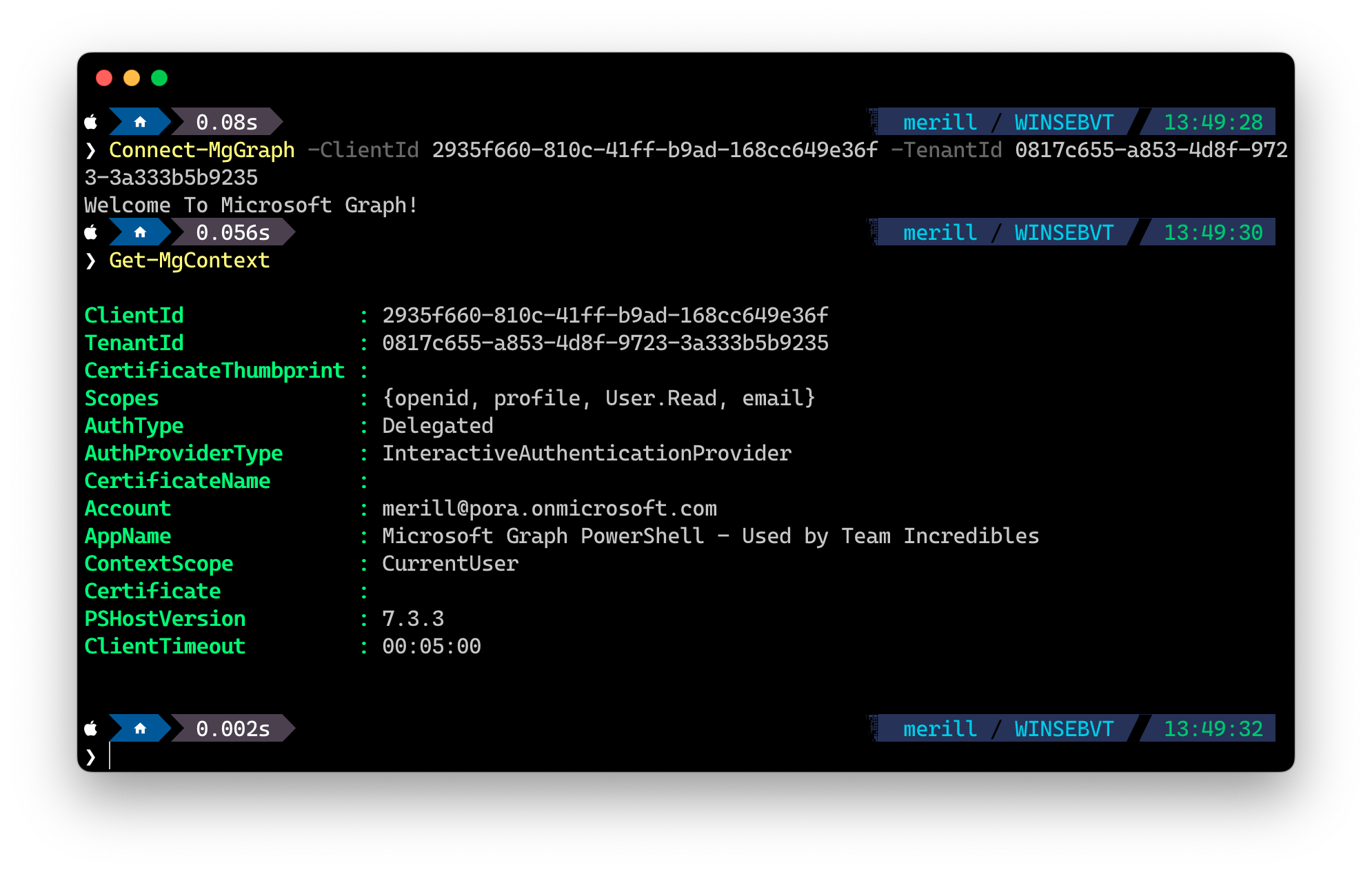
Now you can use this app instead of the default one by connecting with
Connect-MgGraph -ClientId <Your new app clientid> -TenantId <your tenant id>
Here are a few screenshots to help guide you.
Remember to use the ClientId and TenantId parameters when signing in.
Restricted user access
I would also recommend limiting the users that have access to these Graph PowerShell applications. To do this browse to the Enterprise Applications [adapps.cmd.ms](https://adapps.cmd.ms] blade, select the app and in Properties set Assignment required? to Yes. Then grant access to the required folks from the Users blade.
Windows PowerShell 5.1
The steps above will get you working with PowerShell 7, which is what you SHOULD be using. In the unfortunate event that you are stuck with Windows PowerShell 5.1 you need to do one more thing.
- Open the app you just created in App registrations [adappreg.cmd.ms]
- Select Authentication
- Check https://login.microsoftonline.com/common/oauth2/nativeclient
- Click Save
